Is Your Smartphone the Spy In Your Pocket?
[et_pb_section fb_built=”1″ _builder_version=”3.0.47″ custom_padding=”36px|0px|29px|0px|false|false”][et_pb_row _builder_version=”3.0.48″ background_size=”initial” background_position=”top_left” background_repeat=”repeat”][et_pb_column type=”4_4″ _builder_version=”3.0.47″ parallax=”off” parallax_method=”on”][et_pb_image force_fullwidth=”on” _builder_version=”3.19.11″ src=”https://totalitysolutions.org/wp-content/uploads/2019/02/gilles-lambert-8649-unsplash.jpg” admin_label=”Image”][/et_pb_image][et_pb_text _builder_version=”3.19.11″ text_font=”||||||||” text_font_size=”18px”]
We’ve all had it happen to us, even if we didn’t take much notice.
You’re venting to a friend about your least favorite coworker- could he just FOR ONCE not heat his leftover fish in the breakroom microwave?- and within 30 minutes an ad pops up in your Facebook feed that has an eerie connection to your recent conversation.
An odor-eliminator. Or a microwave sale. Or a blog dedicated to improving happiness and wellbeing in the workplace.
Maybe you just scroll past and think, “Huh, weird.”
But let’s stop for a second and really think about this.
All you did was carry on a normal conversation. Your iPhone was just sitting in your back pocket or purse. Yet somehow Facebook captured the key words of your conversation, converted them into data, and slapped highly customized marketing ads directly into your live feed.
It’s one thing to see Facebook ads for dog food after you order your Golden Retriever’s kibble on Amazon- we’re all pretty used to this convergence of internet usage habits and marketing- but it’s infinitely stranger to see it happen when the words are coming out of your mouth (and never typed into your phone!) during any normal part of your day.
So let’s break this down- are you just paranoid, or is your phone really listening to and using your every word?
What Do the Experts Say?
Cell phone manufacturers, of course, deny that your phone can listen to your conversations or speech without your consent.
Representatives including Marsha Blackburn and Robert Latta wrote to Apple’s CEO Tim Cook and Alphabet CEO Larry Page back in July 2018 to express their concerns that smartphones could “collect ‘non-triggered’ audio data from users’ conversations near a smartphone in order to hear a ‘trigger’ phrase, such as ‘Okay Google’ or ‘Hey Siri.’”
Apple responded with claims that iPhones never record audio while listening for commands. This may be true, but it doesn’t address the fact that third-party applications can still gain access and use ‘non-triggered’ data without your knowledge or consent. Apple can’t control exactly how apps like Facebook utilize data, and they can’t ban every app that quietly breaks the rules.
The Wall Street Journal agrees. It reported, “Facebook is now so good at watching what we do online- and even offline, wandering around the physical world- it doesn’t need to hear us. [Yet they do.] Advertising is an important staple of the free internet, but the companies buying and selling ads are turning into stalkers. We need to understand what they’re doing, and what we can- or can’t- do to limit them.”
Creepy Examples
Still not convinced that your cellphone is tuned to your every word? Consider this.
I had a conversation at the beginning of December with my husband. The daycare provider for our daughter had to relocate suddenly and unexpectedly, leaving us with two full-time jobs and zero childcare. Not the best situation.
We went back and forth trying to discuss our options, but couldn’t agree on a solution. So I sunk into the couch, frustrated and upset, and opened Facebook to mindlessly scroll through my live feed.
Can you guess the very first ad that popped up as I scrolled?
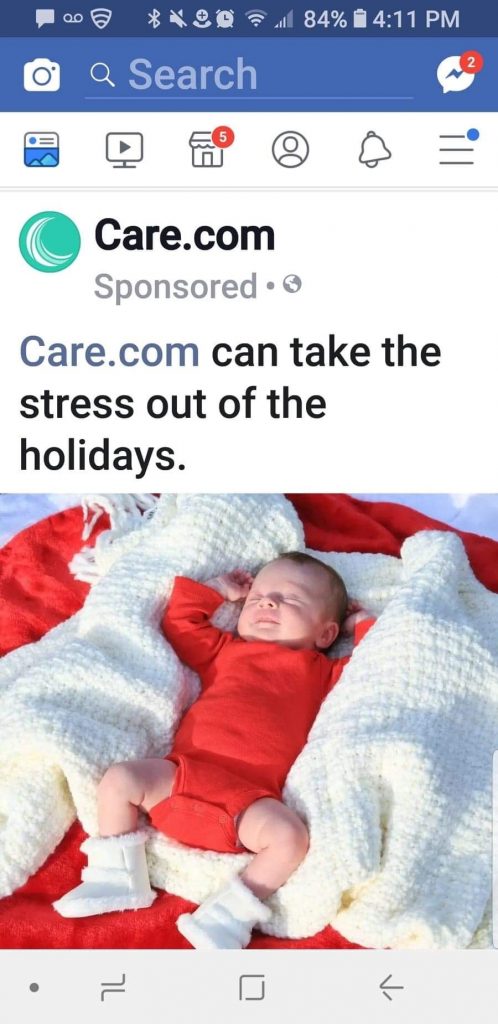
What do you know, a potential solution to the exact problem my husband and I had just been discussing verbally.
That’s far from the only proof that my iPhone- and yours, too!- is listening to conversations and sending keyword data to create targeted marketing.
I had an argument with my son just this morning because he wouldn’t get out of bed to walk the dog. I spewed out a parental lecture about the responsibilities of walking the dog and staying consistent to his schedule, then stomped out to walk the darn dog myself. When I headed back inside and glanced at Facebook, take a wild guess at the advertisement I saw after a few scrolls.
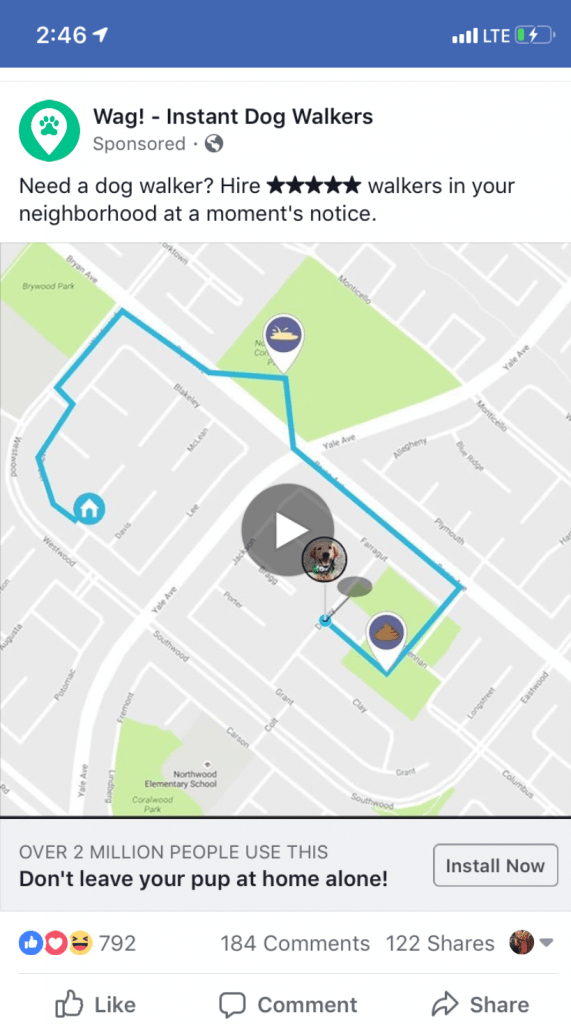
No, this is definitely NOT our collective imagination at work. Our cell phones are listening to us, and short of putting your phone in a glass of water and walking far, far into the middle of the forest to have a conversation, this is our new 21st-century reality.
Short of deleting your Facebook app and disconnecting from your smartphone, your best protections include strict privacy settings, precautions, and self-education.
[/et_pb_text][et_pb_button button_url=”https://totalitysolutions.org/services/cctv/verkada-security-cameras/webinars/” button_text=”Free Webinar: Intro to Cloud Security” button_alignment=”center” _builder_version=”3.19.11″ custom_button=”on” button_text_color=”#ffffff” button_bg_color=”#6eba01″ button_border_color=”#6eba01″ button_text_color_hover=”#6eba01″ button_text_size__hover_enabled=”off” button_one_text_size__hover_enabled=”off” button_two_text_size__hover_enabled=”off” button_text_color__hover_enabled=”on” button_text_color__hover=”#6eba01″ button_one_text_color__hover_enabled=”off” button_two_text_color__hover_enabled=”off” button_border_width__hover_enabled=”off” button_one_border_width__hover_enabled=”off” button_two_border_width__hover_enabled=”off” button_border_color__hover_enabled=”off” button_one_border_color__hover_enabled=”off” button_two_border_color__hover_enabled=”off” button_border_radius__hover_enabled=”off” button_one_border_radius__hover_enabled=”off” button_two_border_radius__hover_enabled=”off” button_letter_spacing__hover_enabled=”off” button_one_letter_spacing__hover_enabled=”off” button_two_letter_spacing__hover_enabled=”off” button_bg_color__hover_enabled=”off” button_one_bg_color__hover_enabled=”off” button_two_bg_color__hover_enabled=”off”][/et_pb_button][/et_pb_column][/et_pb_row][/et_pb_section]


